Pricing for Leopard. OSX 10.5
As seen on engaget:
Steve Jobs sez- "We've got a basic version that will cost $129, we've got a Premium Version which will cost $129..." laughter and applause. "We've got a business version! $129. Ultimate version! We're throwing everything into it, it's $129." Can't even hear Steve, too much applause. "We think everyone's going to buy the ultimate version."
Var scope checker revised and has a new home.
Jim Collins added a file browser to the Var Scope Checker originally authored by Seth Petry-Johnson. The code is now on Google Code, since Seth's website is REALLY down now.
New Scorpio/CF8 Yahoo Pipe
I am still wading through all of the new Scorpio/CF8 information. There is a lot of it and in order to get a better handle on all the topics and postings, I created a new Yahoo Pipe. The full URL is: http://pipes.yahoo.com/pipes/pipe.info?_id=4Awn2KYW3BG_hwQ5y6ky6g
I picked the top 8 blogs for Scorpio news based on an unscientific cruise through the ColdFusion Yahoo Pipe from Brian Rinaldi. There are blogs I have missed so if you know of a good resource for Scorpio/CF8 postings, please leave the feed URL in a comment.
I want to be strict on this one and keep a valuable signal to noise ratio. My own blog is not included in this feed yet, because I haven't posted anything significant on Scorpio/CF8.
So let us make this Scorpio specific please. If you have a Scorpio feed, please submit that one rather than your generic feed URL.
Think you are having a bad day, read this!
PAW PAW, Mich. - A man was taken on a wild ride when his wheelchair became lodged in the grille of a semitrailer and was accidentally pushed down a highway for four miles at about 50 mph, authorities said.
The police statement:
If this was me, the police would have said: "The man was visibly upset and needed several changes of shorts"
You can read the rest of the story for a picture and more details.
Scorpio Beta works with Apache 2.2.4.
Just a quick note to say I was able to get CF 8 working on a fresh install of Apache version 2.2.4.
A few quick observations:
- During the CF install, I got a nice message reminding me to stop ColdFusion MX 7 Search Server
- After CF finished, I had to run the Web Server Configuration Tool again for everything to work
- I also had to open Port 51800 on my local firewall. I suspect this is JNDI.
My initial impressions? The installation process handled the above issues gracefully. This doesn't feel much like beta software... Remind me to tell you about an experience I had with a SQL Studio Express CTP beta once.
Editors note: I suppose I will never be hired by microsoft if I keep making these sorts of comments
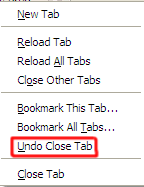
Secret 1337 Trick - Undo Close Tab in Firefox
I just found an interesting feature in Firefox 2. If you have an open tab, then close it, you can right-click the tabs and choose 'Undo Close Tab' and the banished tab will return.
Update:
Jim Priest, who turned me on to the Microsoft Update Reboot Fix points out that the following key combos work:
CTRL+T = new tab
CTRL+SHIFT+T = restore last closed tab
I've use CTRL+T countless times. It never dawned on me to try CTRL+SHIFT+T. Thanks again Jim!
Wishlists come true. Thanks Adobe!
Does anyone remember my posting a while ago about Adobe purchasing Flex books from Amazon Wishlists? I remember quite a few people doubting it was true. When I originally heard the news, I immediately set up a wishlist and added every Flex resource I didn't already have.
After my nice long vacation in the Florida Keys, I came home to a nice surprise! A package from Amazon containing the Lynda videos for Flex!
So, yes it is true. Adobe isn't just going Mad Hatter, of course. I imagine they have a budget and they dole out some books from time to time. I am very happy to be the recipient.
Turns out I already have the Lynda Videos. I was slow in removing them from the wishlist. The only proper thing for me to do was give them to some other deserving soul. Sean has agreed to host a 1,000,000 hits contest for the Videos. You can find details of the contest at Sean's blog.
A big thank you to Mike Potter and the Flex.org team for their continued community support.

Anatomy of an SQL Injection Attack
Security is everyone's problem. It is important to be aware of issues that can foster security violations in software. Buffer Overflows, a common software security hole, arise from the length of input not being checked. When the input is larger than the memory allocated, the input data can spill over into unintended memory addresses. By appending a command with the correct offset, it is quite possible to push the command into memory space with high level privileges and execute.
In a buffer overflow attack, often the application accepting the input is running under reduced privileges. Because the input overflows the given memory address, it matters not that the input originated from a low privilege application, but rather the actual memory address where the command is stored and executed.
SQL injection is another type of attack and shares a common root with Buffer Overflow attacks. When input is not properly evaluated and filtered, bad things can happen. In an SQL injection attack, the attacker appends SQL statements to input. Here is a simple query:
2FROM Users
3WHERE UserID = 1
Here is an example of appending a command to an SQL statement.
2FROM Users
3WHERE UserID = 1; DROP Users;
In the last example, an SQL command to drop the users table was added. Imagine for a moment the URL to access a user profile. http://someserver/index.cfm?userID=1 The userID is appended to the URL and is undoubtedly passed to a query in the application that returns the profile associated with UserID 1.
To create an SQL Injection attack with the URL above, we could simply try the following URL: http://someserver/index.cfm?userID=1;drop users When the application substitutes the userID value of 1;drop users in the query, there are actually two statements to be executed. Firstly, the command to return the data from the users table associated with userID 1. Secondly, the command to drop the whole users table.
Pragmatically speaking, there would be little to gain by dropping the users table apart from vandalism. That being said, there are thousands of 5kr1pt k1dd135 whom would be delighted in dropping your users table for you and then bragging to their little wanker friends about how they trashed your server. Still, not much of a security risk? Let us try another angle.
Suppose for a moment a site that charged a lot of money for access to data. Users periodically purchased subscriptions and your organization was making millions. Inside the database was a users table with the field of 'ExpirationDate' representing the date the subscription would need renewal. Shall we form an attack to give us a 20 year subscription?
This is the SQL we wish to execute
2FROM Users
3WHERE UserID = 1; update Users set ExpirationDate = '5/5/2027';
Can you guess what the URL string would look like?
If you guessed: http://someserver/index.cfm?userID=1;update users set expirationdate = '5/5/2027'
Then you are close. We may need to massage the url a little, or find a text input to put our command if the spaces and quotes are not respected.
So we can bump our subscription up 20 years or so. What else can we do? Let us try to add a user.
This is the SQL we wish to execute
2FROM Users
3WHERE UserID = 1; insert into Users (username, password, expirationdate) values ('imahaxor','inyourbox','5/5/2027');
http://someserver/index.cfm?userID=1;insert into Users (username, password,expirationdate) values ('imahaxor','inyourbox','5/5/2027');
Now in place of just extending a subscription, the attacker has a new account that won't expire for a while yet. Not a pretty picture is it?
How can you defend against SQL injection attacks, you ask? There are some best practices you may follow to reduce your attack surface. Let us look at a few:
- Reduce the privileges given to the SQL user of your application. If the application never needs to insert into a particular table, then remove that privilege.
- Check your input values. If you are expecting a number, add val() around the value. In the case above, a simple val() statement turns a malicious statement into a simple 0. We all like 0, right?
- Use prepared statements. Adding cfqueryparam values to your dynamic query values adds great protection. Apart from escaping malicious characters, the prepared statement treats the value as a value, not a string of text to be executed by the SQL engine.
While software is extremely difficult to secure completely you can remove a giant risk by gaining understanding of SQL Injection Attacks and using the techniques above.
Below are some examples of a recent attempt to use SQL Injection on my blog. This attack was not very sophisticated, but could have disrupted the services of this blog.
WOT - Florida Keys Pictures on Flickr
I put a few pictures on Flickr from my recent Florida Keys Vacation. If any one would like to chip in $700k I'll be happy to buy a house and a boat and take care of them both. I cook some mean Quesadillas and Fish Tacos.
Bears in the neighborhood.
At the moment, I live in New Jersey, right where the suburbs of the 'city' meet the countryside. New Jersey is remarkable for a lot of reasons. Today, let us talk of my favorite topic, Bears.
Not the Chicago Bears, mind you, I mean the black fuzzy bears that look so cute you want to reach out and pet them. Of course, you need to have a friend along. Afterwards someone will be transporting parts of your carcass to the hospital. Who better than a friend, right? I digress, Death and Dismemberment notwithstanding, the bears are seriously cute.
For some reason, I seem to attract bears. Maybe I need to change my hair care products, or finally cease wearing the sneakers I've had for 4 years. Regardless, I have 6 bear sightings in less than a year.
I have seen 6 wild bears. 3 I saw on foot. 3, I just saw in my neighborhood as I was leaving for a sandwich.
Professional Bearologists will tell you to leave the bears alone. They say do not follow the bears, stay far away. This is precisely what I did not do.
I followed the bears (doing 1MPH in my car with the window open) across three lots trying to take a sensible picture with my camera phone. I was sure they would jump through the window and start mauling at any second. The thought of getting up close pictures was worth the risk.


As you can tell from the stellar image quality, it was not worth the risk. I should have left the phone in my pocket and just watched the bears.
So now, in place of getting a new MacBook, I am looking for a new cellphone/pda with an excellent camera. I am leaning towards the Blackberry Pearl
Any recommendations, suggestions, personal anectdotes?

 Posted By : Dan Wilson
Posted By : Dan Wilson  June 11, 2007 2:31 PM
June 11, 2007 2:31 PM

 Suscribe
Suscribe Follow Us
Follow Us Contact
Contact